Machine learning is undoubtedly the hottest topic in cybersecurity today – but it’s also among the most over-hyped. Not because it won’t live up to its promise, but because it’s being marketed so pervasively and even inappropriately.
Machine learning is undoubtedly the hottest topic in cybersecurity today – but it’s also among the most over-hyped. Not because it won’t live up to its promise, but because it’s being marketed so pervasively and even inappropriately.
It’s no surprise to see such buzz around a potentially game-changing class of technology. Every major innovation goes through a lifecycle of curiosity, testing, skepticism, initial traction, and – if it can cross the chasm – widespread adoption. But the process is messy, nonlinear, and unpredictable.
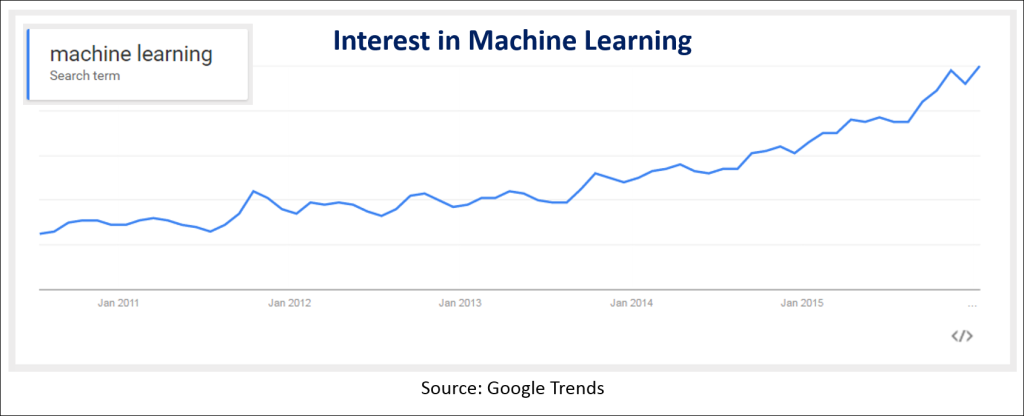
Interest in machine learning today is growing by leaps and bounds, fueled by an exploding set of ML applications. Facebook’s Bot Engine, Google’s AlphaGo, Microsoft’s image, speech, and language capabilities, and many others demonstrate how broad the impact could be.
Now add in the claims around machine learning for security – some valid, some overstated – and it’s easy to see how all the hoopla can lead to cynicism.
As John Melas-Kyriazi of Spark Capital wrote, “It’s easy to find companies building weak ML-driven user experiences, turning off early adopters. Others are building products centered around gimmicky ML features that won’t create any sort of long term barrier to competitors.”
In other words, machine learning’s reputation is being sullied by wannabes.
The good news is this won’t last. In cybersecurity, those unable or unwilling to explain their ML technology and prove its value will get eclipsed by those who do. Transparency and proof are becoming table stakes.
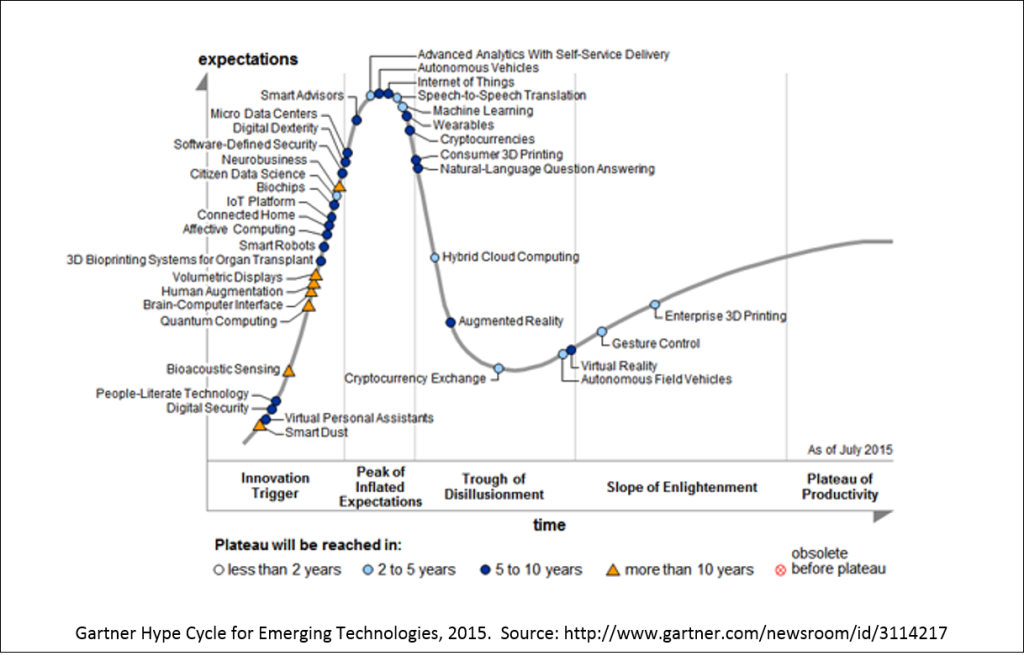
Gartner charts this in their Hype Cycle for Emerging Technologies, and perched right at the Peak of Inflated Expectations is machine learning – as we would expect. Although it will take time for ML to “grow into” these expectations, there’s little doubt it will.
What does it all mean?
Information security teams should approach security machine learning like any promising new class of technology:
- First, no science experiments – you’re not Google. Focus on the top business problems you need to solve, and consider how commercial ML products might address them today. If a technology doesn’t align to those priorities, move on.
- Probe for what’s real and how it would fit into your environment.Is the technology stable, effective, intuitive? How easy is it to deploy and manage? Talk with your early adopter peers to learn about their experiences. Demo and test; ask vendors the hard questions you want to understand.
- Have patience. The reach and impact of machine learning in IT security will play out over years. If you’re interested in a particular approach or technology but feel it isn’t ready yet, that’s okay. Watch as it matures, monitor your peers’ experiences, and when the time is right take a closer look again.
Fact or Fiction?
For more insights on separating fact from fiction in security machine learning, check out this short 4-question quiz I contributed for Buzzfeed.
Safe passage in your machine learning journey!