This was originally published on invincea.com on September 11, 2015.
When it comes to home security, I love my Dropcam. It’s easy to set up, captures a brilliant high-resolution image, and provides an intuitive interface for me to view activity.
But if it were just a video camera with a DVR, it wouldn’t be worth the price. Simple video recording and webcasting aren’t the reasons why I bought my Dropcam, nor would it have enabled Dropcam to build a $500 million business.
What adds real value is the product’s intelligent detection. Dropcam doesn’t just show me a moving image; it extracts context from that data stream.
I can tell Dropcam if I want to be alerted to motion – in a specific part of the video frame, during particular days and time windows. I can also receive sound-based alerts and adjust the sensitivity of the device’s microphone to avoid false positives.
Suddenly this toy became a real security tool. I can target my monitoring, eliminate false positives, and go about my day until something noteworthy happens. Dropcam doesn’t just silently record data, which I would then have to search days after an intruder had stolen my valuables.
Dropcam illustrates well the Second Law of Intrusion Detection: Detection requires intelligence. Building on the First Law of Intrusion Detection (You can’t detect what you can’t see), this law establishes that while “seeing” activity on your endpoints is a necessary start, your security solution must also extract meaning from that activity in real time to identify attacks. It must apply “intelligence” to raw information, to generate meaningful insights in actionable timeframes.
A detection solution must apply intelligence to raw information, to generate meaningful insights in actionable timeframes.
In contrast, some products are being positioned today as “threat detection” solutions when they’re really only suited for post-breach confirmation. The problem with these tools – and let’s call a spade a spade: Bit9 + Carbon Black and Tanium, among others – is you have to know what you’re looking for to find anything. In the case of simple attacks, such a solution might find a known Indicator of Compromise – for example, a month-old domain – in your endpoint activity data store, after a third-party threat intelligence feed tells it to look for the domain. But when a cyber-crime gang targets your organization with unknown malware spread via hyper-targeted malvertising, hosted on short-lived burner domains, the post-breach confirmation tool will have no chance of detecting that in an actionable timeframe. In other words, what you actually have is something closer to a DVR that requires intelligence and a good search engine to find out what happened on your network, long after it happened.
If your current detection solution is geared toward massive data collection or endpoint querying without the brains to know what to look for, then it fails to meet the Second Law of Intrusion Detection.
In the first case of massive data collection (let’s just call it DVR’ing), you record large volumes of data about endpoint files and activity, but without an automated way to make sense of it. It sits there until you discover an indicator of breach through other means; then it can help you look for fingerprints. This is retrospective analysis, which in many cases is a study of the historical record, but without the ability to change it. The problem is your adversary has already stolen administrator credentials, mapped your network, and exfiltrated intellectual property – or worse, as in the case of Sony. Such a tool is useful for incident response to figure out what happened and where, but it won’t stop or inhibit compromise. Worse, it often requires expensive storage arrays to maintain the petabytes of raw data needed to DVR an entire network. How does this make any business more secure?
In the case of a querying tool only (a la Tanium), you save on storage but still lack the intelligence and continuous monitoring needed to detect an attack. It can help you find suspicious files or vulnerable applications – after you gather attack details or IOCs from elsewhere. Without intelligence and analytics, there is no timely detection. In 2015, we should expect the network to tell us when there is a problem, rather than having to ask the network if it has a problem and feeding it the problem to search for. This is where big data analytics and machine learning are needed to add brains to what’s essentially dumb search.
Without intelligence and analytics, there is no timely detection.
Fortunately, state-of-the-art approaches for endpoint threat detection can now identify even the stealthiest attacks:
- Data science and machine learning: Thanks to powerful trends such as inexpensive compute resources and developments in deep learning, robust machine learning-based malware detection is now possible.
- Static code analysis: Innovative methods of static software analysis can be used to reveal the true nature of unknown programs, providing a breakthrough in the detection of unknown malware.
- Cloud-based analytics for crowdsourced intelligence: Rather than rely on a single type of analysis, single database of threat intelligence, or single vendor, next-generation endpoint detection solutions use a cloud-based approach to intelligently aggregate the sum total of analytical techniques and databases, including information crowdsourced from enterprises.
- Behavioral threat detection: Using advanced process monitoring, this approach continuously evaluates how each process uses memory, file, and network resources. Operations such as process launches, module loads, registry and file writes, and network connections can serve as triggers for an event, based on context.
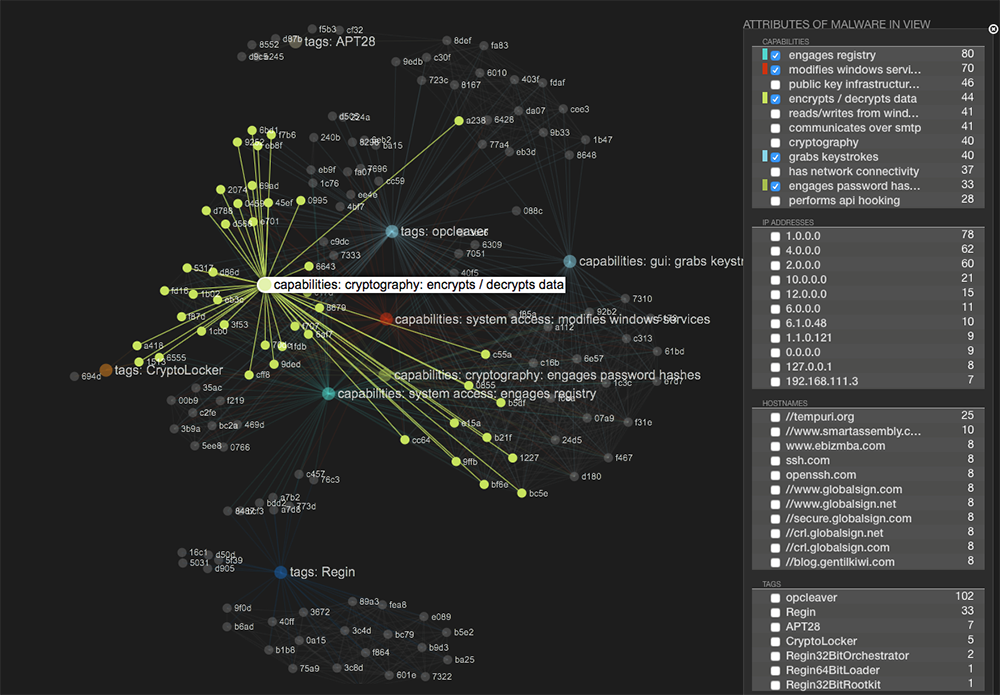
These approaches not only rapidly identify attacks, but also save enormous time by not forcing you to manually search for and investigate suspicious activity. Given the demands on enterprise security teams today, technologies that don’t automate detection – especially those that create added work for security operations – are inefficient and undesirable.
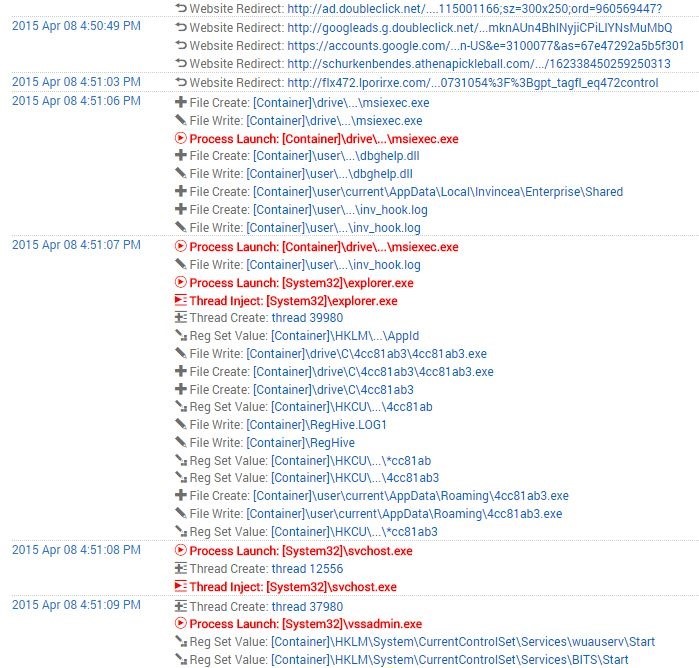
There’s an important role for post-breach confirmation and investigation tools, especially for Incident Response teams and prosecution. Just don’t confuse them with detection solutions or think they will stop the breach. True advanced threat protection tools (ones that follow the Laws of Intrusion Detection) help you identify compromises in real time, so you can isolate, analyze, and eradicate the threat enterprise-wide. The other type helps determine how much damage was done and what remediation is needed. You can make a small investment up-front to counter threats in real time, or you can make a massive balloon payment on the back-end with IR professional services and tools.
As you evaluate your security capabilities and needs heading into 2016, identify and prioritize your gaps along the Prevent / Detect / Respond continuum. If breach detection is lacking, make sure you find a solution that’s fit for purpose.
It’s not about data. It’s about insight, which comes only from intelligence.
